Context and Purpose
 The Belgian eID is a classic smartcard integrating standard public-key cryptography technology. One of its functionalities allows its owner to sign digital documents. However, if the owner wants to sign 100 documents, either he has (besides selecting each document separately) to type in his PIN code a 100 times as well, or he is forced to use a software that caches his PIN code that is then used to perform as many signatures as documents to sign.
The Belgian eID is a classic smartcard integrating standard public-key cryptography technology. One of its functionalities allows its owner to sign digital documents. However, if the owner wants to sign 100 documents, either he has (besides selecting each document separately) to type in his PIN code a 100 times as well, or he is forced to use a software that caches his PIN code that is then used to perform as many signatures as documents to sign.
In this context of digital signatures, Smals proposes the signature software SmalsBeSign able to perform secure batch signing. The software generates a digital signature of a set of documents, using the Belgian eID. The PIN code is asked only once and used only for such a unique signature. This way, the user is in full control of his eID, of his PIN code and of his signature. This is in opposition with many other softwares where the user is not in control of the material (e.g. when the PIN code is cached). Note that, even if the software computes one unique signature for a set of documents, it generates an independent signature result (i.e. a zip file) for each document.
How SmalsBeSign works
Signing documents
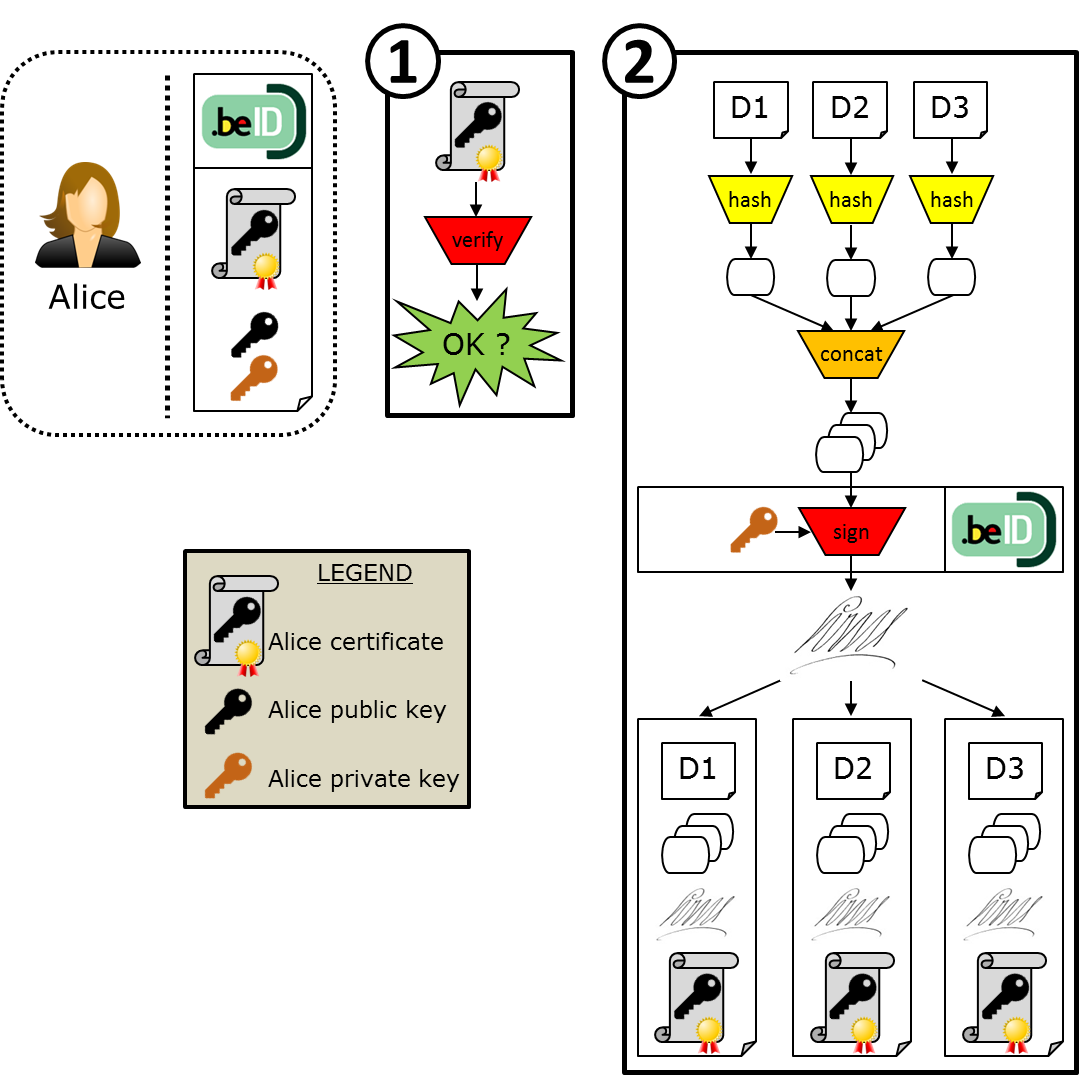
Let’s imagine that Alice wants to sign 3 documents D1, D2 and D3. In order to do so, the software first verifies that the certificate chain of trust of Alice’s plugged eID is correct, including, when there is an internet connection, whether the certificates are revoked or not on the official webpage.
Then, Alice provides the three documents to SmalsBeSign. The software then computes the hash of each document, respectively H1, H2 and H3. The hash algorithm used at this step is SHA-256. Then, SmalsBeSign concatenates all the hashes. The resulting value H1||H2||H3 is called the “master digest”.
SmalsBeSign then asks Alice’s eID to compute the signature of the master digest with Alice’s private key. The signature algorithm used at this step is SHA1withRSA (OID = 1.2.840.113549.1.1.5).
Finally, SmalsBeSign outputs a zip file for each signed document that contains the following:
- the README file explaining how to use the software,
- the document (either D1, or D2, or D3 in our example),
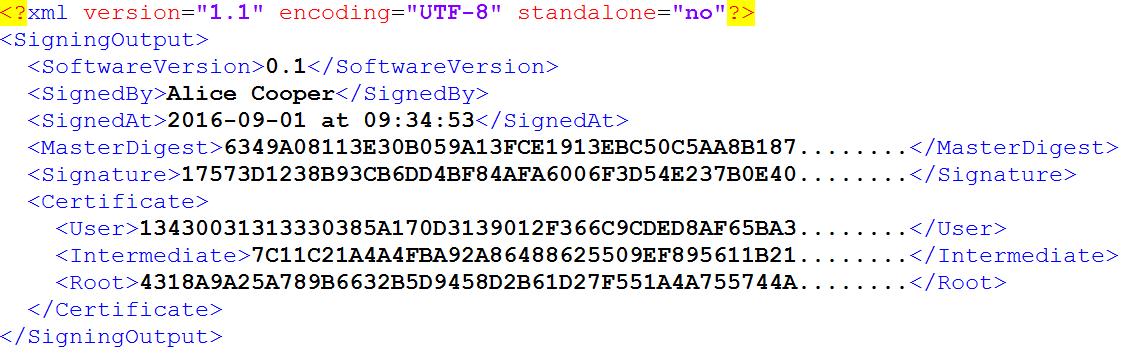
- the signature file in XML format that contains
- the version number of the software SmalsBeSign used to compute the signature,
- the user whose eID has been used to compute the signature,
- the system date when the signature has been computed,
- the master digest,
- the signature,
- the 3 certificates that form the certificate chain of trust of the user (Alice in our example) certificate: the user certificate, the intermediate certificate, and the root certificate.
Alice can then send the zip files of documents D1, D2, D3 to some receivers who will be able to verify the signatures using the software SmalsBeSign, as explained in the following.
Verifying signed documents
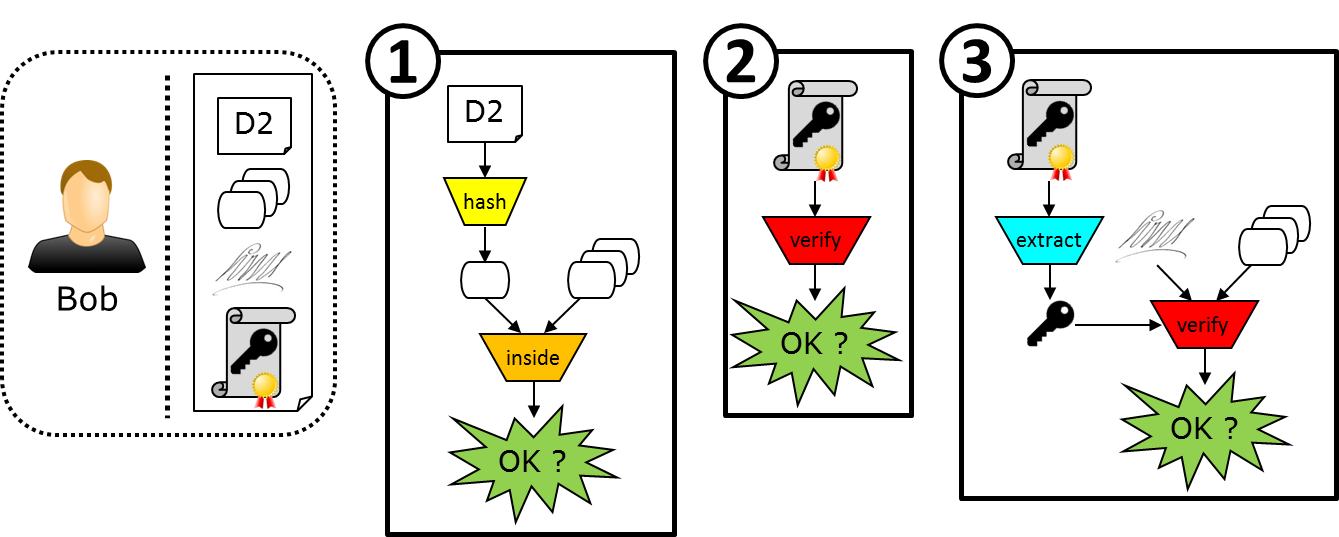
Let’s imagine that Bob wants to verify a zip file sent by Alice containing a document D2 and a signature file. First, SmalsBeSign hashes this document D2 contained in the given zip file. It then verifies that this hash value is inside the master digest (extracted from the signature file). If not, it means that the information contained in the signature file does not correspond to the document D2. Thus the verification fails and stops.
If the hash value is found in the master digest, then SmalsBeSign checks two more things. First, it verifies if the certificate chain of trust of Alice’s eID (contained in the signature file) is correct, including, if there is an internet connection, whether the certificates are revoked or not on the official webpage. Then, it verifies if the signature of the master digest is valid with Alice’s public key (this key is stored in the user certificate field of the signature file).
If all these verifications succeed, then Bob is ensured that the signature of the document D2 is correct and performed by Alice.
How to use SmalsBeSign
Signing documents
- Download and install the software by following the instructions provided in the next section “Download SmalsBeSign”.
- Open/run the software “SmalsBeSign”.
- If you are behind a proxy, click on “File > Settings”, then fill the proxy settings and check “Use proxy”.
- Click on “Sign files” or “Task > Sign”.
- Select the documents to sign with “Select files”.
You can preview the PDF documents on the right part. Other types of documents can be opened with their default software (e.g. Microsoft Word or PowerPoint). - Connect a card reader and put the eID card inside.
On the bottom bar, it then indicates that an eID card is inserted into the card reader. - Click on “Sign files”.
- Enter the eID PIN code.
Be careful: you have only 3 attempts to enter the correct PIN code, otherwise the eID card gets automatically blocked (for security reasons). - Choose the folder to store the result files.
- For each document that has been signed, the result file is a zip file (named name_of_the_document.signed.zip) containing:
- the README file,
- the original document,
- the signature file in XML format.
At the end of the process, SmalsBeSign outputs a message saying that the zip file(s) has(have) been correctly saved. Since the software checks if the chain of certificates is correct, it may output an ORANGE / WARNING when it could not verify one or several problematic certificates because:
- either there was no internet connection allowing to check the validity and revocation of certificates (e.g. no connection, or behind a proxy that hasn’t been or could not be configured in “File > Settings”),
- or the problematic certificate(s) has(have) already been revoked.
VERIFYING SIGNED DOCUMENTS
- Download and install the software by following the instructions provided in the next section “Download SmalsBeSign”.
- Open/run the software “SmalsBeSign”.
- If you are behind a proxy, click on “File > Settings”, then fill the proxy settings and check “Use proxy”.
- Click on “Verify signed files” or “Task > Verify”.
- Select the zip files to verify (only with .zip extension) with “Select zip files”.
You can preview the PDF documents that are inside the zip file on the right part. Other types of documents can be opened with their default software (e.g. Microsoft Word or PowerPoint). - Click on “Verify signed files”, and the result is simply outputted on the screen.
Depending on the success of the verifications performed by the software, SmalsBeSign may return several possible outputs.
- GREEN / OK: Every verification is OK.
- ORANGE / WARNING: During the chain certificate verification, the software could not verify one or several problematic certificates because:
- either there was no internet connection allowing to check the validity and revocation of certificates (e.g. no connection, or behind a proxy that hasn’t been or could not be configured in “File > Settings”),
- or the problematic certificate(s) has(have) already been revoked.
- RED / FAILED: Either the master digest, or the chain certificate, or the signature is not correct.
How to use the software (in Video)
For a functional explanation of SmalsBeSign, please watch the following video.
Download SmalsBeSign
The different editions of the software can be found below. They all work with internal or external Belgian eID card readers and appropriate middleware already installed on the computer.
Disclaimer
Due to several reasons, we decided to not further improve our software (e.g. timestamping…), which remains as our first version 0.1. So as from september 2017, the SmalsResearch certificate used for code signing will no longer be renewed and, during the installation of our application on your system, Microsoft will give a warning that our identity can’t be guaranteed. Please ignore this warning if you want to install the software, but be aware that our software remains on version 0.1!
.
 SmalsBeSign Installer version (Windows 7.0 or higher, embeds Java 1.8.0_101)
SmalsBeSign Installer version (Windows 7.0 or higher, embeds Java 1.8.0_101)Smals Research
2016/09, v 0.1