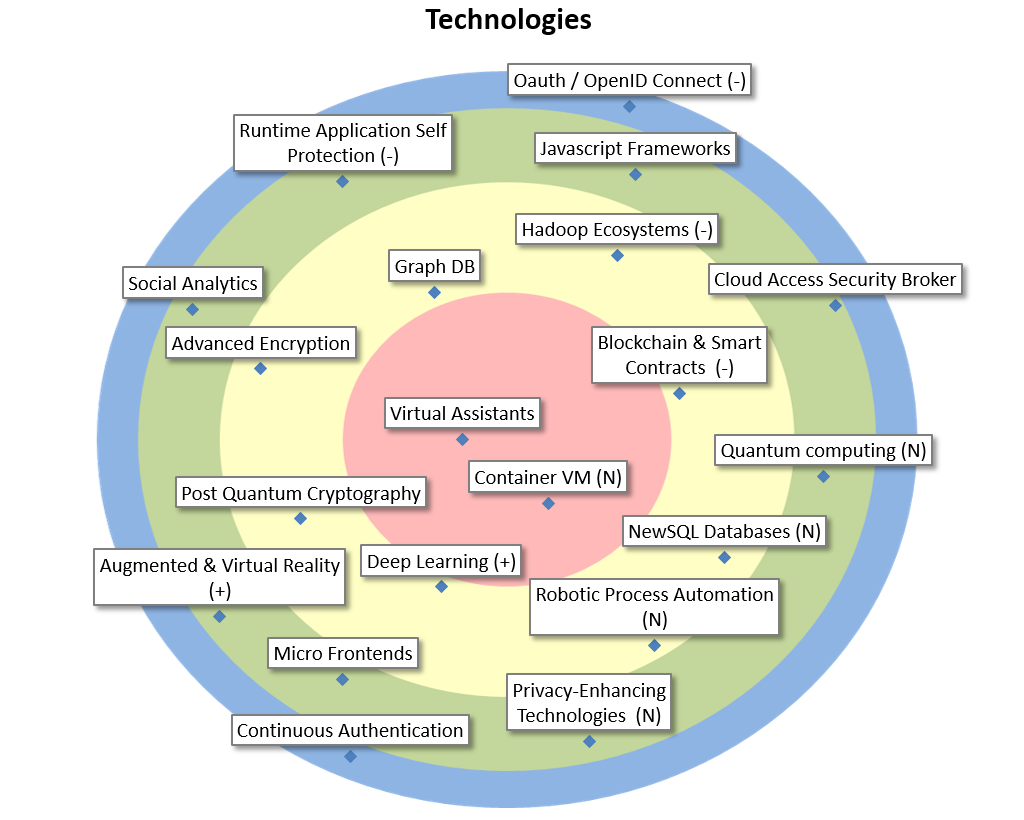
| Virtual Assistants |
Virtual assistants are computer programs that automatically reply to questions or utterances. The basic channel of communication is a conversational interface, that accepts chat or speech. Possible applications are: website guidance, helpdesk assistance, or simplification of procedure. |
| Container VM |
Containers are not perfectly isolated, virtual machines are toon heavyweight. Container VM technology aims to bridge the gap by making very lightweight but well isolated vm’s, perfectly suited to run a container. Useful for multitenant Kubernetes and FPaaS platforms. |
| Blockchain & Smart Contracts |
Blockchain & smart contracts offer autonomous (shared) storage and autonomous computation in a network. Hence, no one can change the data or influence the computation. This offers new possibilities for distributed trust and to simplify existing applications & architectures. |
| Hadoop Ecosystems |
Hadoop Ecosystems implement Big Data distributed storage (HDFS), access (Hive, Impala), distributed computing (MapReduce, Spark), transfer (Sqoop, Kafka, Flume), configuration, monitoring, and management modules, in one integrated environment consisting of several nodes. |
| Graph DB |
Databases based on and/or oriented towards graphs, with nodes (entities) connected through edges (relations). They are very useful in graph analytics, but could also serve in miscellaneous production systems. |
| Advanced Encryption |
Cryptography is a powerful toolbox but awareness of its potential is yet small. Examples are elliptic curve cryptography (as an alternative to RSA), format preserving encryption, authentic encryption and ring signatures. |
| Post Quantum Cryptography |
Cryptographic algorithms thought to be secure against an attack performed by a quantum computer. |
| Deep Learning |
Important focus area of AI. Architectures such as Recurrent/Convolutional Neural Nets, GANs, etc. learn hierarchical representations of the data, corresponding to different levels of abstractions, largely from the raw data. Toolkits include TensorFlow, Caffe, Keras,… |
| Robotic Process Automation |
Robotic Process Automation is a process automation technology in which software robots can take over keyboard/mouse and other controls to simulate the work of human workers, enabling automation without altering existing systems. |
| NewSQL Databases |
NewSQL Databases combine the scalability and performance of NOSQL DB’s with the ACID principles of RDBMS. Like the traditional DB’s, they support the relational model and SQL. This makes them more suited to replace these DB’s in older applications being re-engineered to increase resilience. |
| Cloud Access Security Broker |
On-premises or cloud-based security policy enforcement point, placed between cloud service consumers and cloud service providers to combine and interject enterprise security policies as the cloud-based resources are accessed. |
| Javascript Frameworks |
JavaScript has become the most important language on the web (even on the server), and new, powerful frameworks continually evolve to give developers more effective options for web development. |
| Runtime Application Self Protection |
Runtime Application Self Protection (RASP) is a security technology that is built or linked into an application or application runtime environment, and is capable of controlling application execution and detecting and preventing real-time attacks. |
| Social Analytics |
The automatic processing and analysis of data from internal and external social media to extract useful information. Most of Big Data Analytics solutions have connectors to exploit these kinds of resources. |
| Augmented & Virtual Reality |
UI technologies offering an immersive experience, using altered or completely simulated environments in which the users senses virtual entities. Hyped in 2016/2017, yet deployment options in the public sector are not readily apparent. Potential uses in (explorational) Analytics. |
| Micro Frontends |
In analogy with microservices on the server side, micro front-ends allow the piecemeal development and deployment of an end-user application. The success of this technology will be determined by the quality of the frameworks/platforms combining these ‘pieces’. |
| Privacy-Enhancing Technologies |
Privacy-Enhancing Technologies (PET) are the methods of protecting data in accordance with the law. PET uses techniques to minimize possession of personal data without losing the functionality of an information system. |
| Quantum computing |
Quantum computing is computing using quantum-mechanical phenomena, such as superposition & entanglement. It is completely different from binary digital electronic computers based on transistors and capacitors, which is also reflected in new programming languages such as Q#. |
| Oauth / OpenID Connect |
Standards for authentication / authorization relevant in the domains of mobile applications and REST architectures. |
| Continuous Authentication |
Methods for continuous verification whether the same specific person who logged into a device is still using it. |